This is a bit out of left field for my usual content, but I needed to set this up recently and thought that maybe at least one other person would be interested in setting up a Site-to-Site VPN between their Ubiquiti UniFi router and UpCloud VMs.
After spending far too long digging through forum posts and piecing together information from different sources, I’ve got a working setup that I’m pretty happy with, so I thought I’d share it. It may not be exactly the same as your needs, but you can tweak bits as needed.
Full disclaimer, I work for UpCloud, but you can adapt this guide to work with any provider that offers private internal networking like this, you just need to change the IP ranges that you want to work with, the same goes for anyone wanting to do this with UpCloud’s SDN options rather than Utility network, just change the IP range(s) to those of your SDN networks!
Table of Contents
Prerequisites
- UniFi Router/Gateway with Site-to-Site VPN capabilities
- UpCloud VM with Debian/Ubuntu (there’s a 7-day trial available if you want to check it out)
- Public IP addresses for both endpoints (your home internet + the UpCloud VM)
I’m using Ubiquiti’s UniFi Cloud Gateway Ultra for this, as that’s what I have both at home and in the office, but this should work with other UniFi routers too.
The cloud server from UpCloud can be in any zone. I’d recommend choosing whichever is closest to your own location, and you can go with any of the plans. In my testing, I used a €3 DEV plan and everything worked just fine. You just need to ensure that it has a public IP address for you to go through, and then you can have other VMs with UpCloud that don’t have public IPs and access them via the Utility/internal network from your home network!
UniFi Router Configuration
Setting things up on the UniFi side is super straightforward:
- Log in to your UniFi Controller
- Navigate to Settings > VPN > Site-to-Site VPN
- Create a New Site-to-Site VPN
- Select IPsec as the VPN type
- Give it a memorable name!
- Select Route Based if it’s not already selected
Basic Settings
- Server Address: Your UniFi router’s public IP (should auto-populate)
- Remote IP: Your UpCloud VM’s public IP
- Remote Networks: 10.0.0.0/8 (for UpCloud networks)
- Pre-Shared Key: Use the one pre-generated, or generate something strong and note it down
NOTE: If you use 10.0.0.0/8 or anything within it on your home network, you’ll need to amend the Remote Networks list, otherwise, you’ll end up with a conflict and it won’t work!
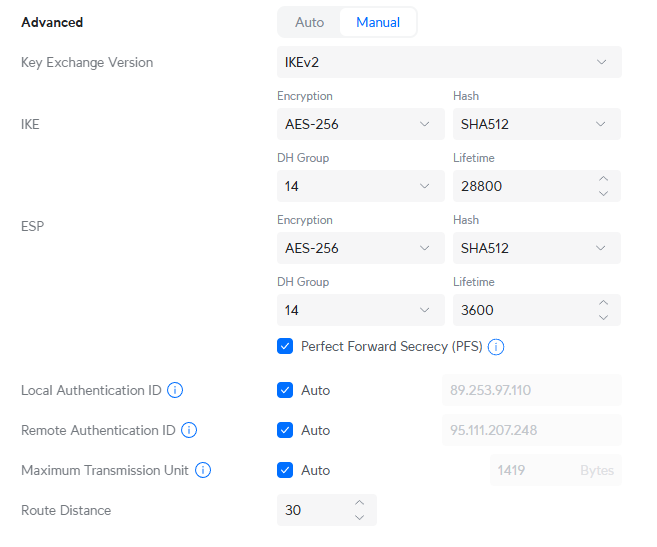
Advanced Settings
We’re going to deviate a little from the Auto defaults with the following:
UpCloud VM Configuration
There are a few things you’ll need to change in the configs below. To make it a bit clearer:
- $YOUR-IP – Your home connection’s public IP address
- $LOCAL-IP-RANGE – Your home network’s IP range
- $UPCLOUD-IP – Your UpCloud VM’s public IP address
- $ROUTED-IP-RANGE – The IP range(s) to route over the VPN
I’m also assuming your utility IP address on the UpCloud VM is on eth1, which is the default. If you’ve changed your network setup, you’ll need to check which interface your utility IP is using.
Install StrongSwan
First, install StrongSwan to handle the IPsec connection:
sudo apt update
sudo apt install strongswanConfigure IPsec
Create your IPsec configuration:
sudo nano /etc/ipsec.confAdd this configuration (changing the variables as needed):
config setup
charondebug="ike 2, knl 2, cfg 2, net 2, esp 2, dmn 2, mgr 2"
conn unifi-to-upcloud
type=tunnel
auto=start
keyexchange=ikev2
authby=secret
# UpCloud VM info
left=$UPCLOUD-IP
leftsubnet=10.0.0.0/8
leftid=$UPCLOUD-IP
# UniFi router info
right=$YOUR-IP
rightsubnet=$LOCAL-IP-RANGE
rightid=$YOUR-IP
# Encryption settings
ike=aes256-sha512-modp2048
esp=aes256-sha512-modp2048
# Perfect Forward Secrecy
pfs=yes
# Additional settings
ikelifetime=28800s
lifetime=3600s
dpddelay=30s
dpdtimeout=120s
dpdaction=restartNow add your pre-shared key:
sudo nano /etc/ipsec.secretsAdd this line (using the same key from your UniFi setup):
$UPCLOUD-IP $YOUR-IP : PSK "your_preshared_key_here"Enable IP Forwarding
Time to let your VM route traffic:
sudo nano /etc/sysctl.confUncomment or add these lines:
net.ipv4.ip_forward = 1
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0Apply the changes:
sudo sysctl -pSet Up the Firewall
We need to allow VPN traffic through:
sudo apt install iptables # if not already installed
sudo iptables -A INPUT -p udp --dport 500 -j ACCEPT
sudo iptables -A INPUT -p udp --dport 4500 -j ACCEPT
sudo iptables -A INPUT -p esp -j ACCEPTMake these rules persist across reboots:
sudo apt install iptables-persistent
sudo netfilter-persistent saveConfigure NAT
Set up NAT for traffic from your UniFi network:
sudo iptables -t nat -A POSTROUTING -s $LOCAL-IP-RANGE -o eth1 -j MASQUERADE
sudo iptables -A FORWARD -i eth0 -o eth1 -j ACCEPT
sudo iptables -A FORWARD -i eth1 -o eth0 -j ACCEPTStart StrongSwan
Finally, start the VPN service and make it run at boot:
sudo systemctl restart ipsec
sudo systemctl enable ipsecTesting the Connection
Check IPsec Status
Make sure your VPN is working:
sudo ipsec statusYou should see something like:
Security Associations (1 up, 0 connecting):
unifi-to-upcloud[1]: ESTABLISHED
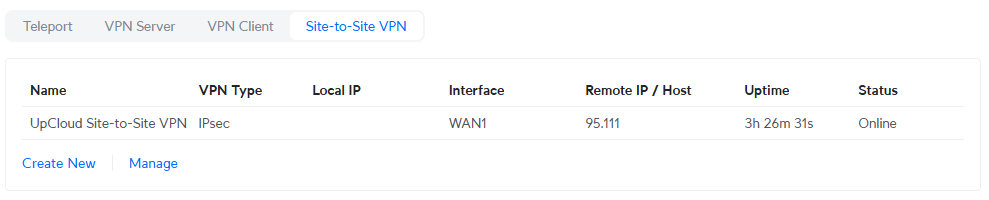
unifi-to-upcloud{1}: INSTALLED, TUNNELWe should also see the following in the UniFi Console
Verify Connectivity
Now let’s make sure traffic is actually flowing:
From UpCloud VM to UniFi LAN:
ping 192.168.1.x # change to an IP on your home networkFrom UniFi LAN to UpCloud networks:
ping 10.x.x.x # change to an IP on your UpCloud network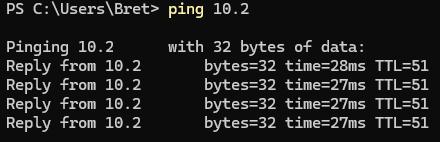
Troubleshooting
If things aren’t working as expected, here are a few things to check:
Look at the IPsec Logs
sudo tail -f /var/log/syslog | grep charonCheck for Traffic Flow
This will show you if packets are moving through the VPN:
sudo tcpdump -i eth0 espIf you don’t see anything while trying to ping across the VPN, something’s not right.
Restart the VPN Service
Sometimes turning it off and on again really does work:
sudo systemctl restart ipsecThat’s it! You should now have a functioning Site-to-Site VPN between your UniFi network and UpCloud VMs. This setup lets you route traffic between your home network and UpCloud’s utility networks without having to list out each specific subnet.